Cryptography Lec 6(Key Agreement Protocol) - Notes
tags: Cryptography NTU
Background
About HSM(Hardware Security Module) - 什麼是硬體安全模組?
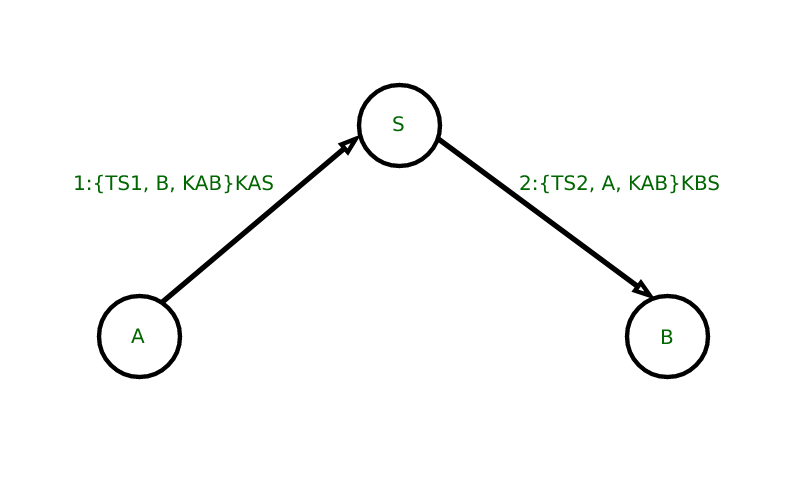
The Wide Mouth Frog Protocol is a computer network verification protocol typically used on unsecured networks. It permits people communicating over a network to verify their identity to each other, it also helps in preventing replay attacks, or snooping and offers detection of any alteration and the prevention of any unwanted reading. This can be demonstrated by means of BAN (Burrows–Abadi–Needham) logic. However, to avoid active attacks, some form of message authentication or authenticated encryption must be used.
The protocol can be specified as follows in security protocol notation, where user A is verifying itself to user B using a server S:
- Where the identities of user A, user B, and the trusted server are A, B, and S respectively.
- Timestamps generated by user A and server S are TS1 and TS2 respectively.
- A Symmetric key KAS that is only known to A and S.
- A generated symmetric key KAB, which will be the session key of the session between user A and user B.
- A Symmetric key KBS that is only known to B and S.
2A → S: A, {T{S1}, B, K{AB}}K{AS} S → B: {T{S2}, A, K{AB}}K{BS}